How Cybersecurity Really Works: Unraveling the Complexities of Digital Protection

In today's digitally driven world, cybersecurity has become an indispensable aspect of our lives. From safeguarding our personal data to protecting critical infrastructure, cybersecurity plays a pivotal role in ensuring our digital well-being and societal stability. Yet, for many, cybersecurity remains an enigmatic field, shrouded in complexity and jargon. 'How Cybersecurity Really Works' is a comprehensive guide that aims to demystify this complex discipline, providing a clear and accessible understanding of its essential principles and practical applications.
Chapter 1: The Cybersecurity Landscape
This chapter sets the stage by exploring the rapidly evolving cybersecurity landscape. It examines the diverse range of threats that confront us in the digital realm, from malware and phishing attacks to data breaches and cyber espionage. The chapter also discusses the key players involved in cybersecurity, including governments, law enforcement agencies, and private-sector organizations.
4.7 out of 5
| Language | : | English |
| File size | : | 7876 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 200 pages |
Chapter 2: The Architecture of Cybersecurity
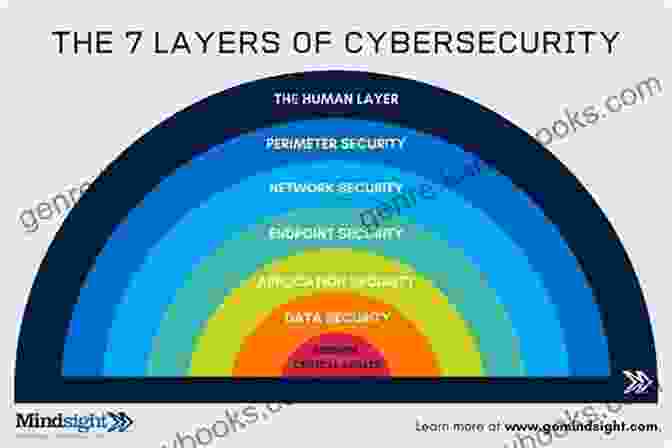
Cybersecurity is not a one-size-fits-all solution; rather, it requires a layered approach that encompasses a wide range of technologies, processes, and policies. This chapter delves into the intricate architecture of cybersecurity, examining the different layers of protection, including network security, endpoint security, application security, and cloud security. It also explores the role of encryption, authentication, and access control in safeguarding data and systems.
Chapter 3: The Human Factor
While technology plays a critical role in cybersecurity, the human factor remains a crucial element. This chapter emphasizes the importance of cybersecurity awareness and training, highlighting the role of individuals in protecting their own devices and data. It also examines the psychological and social aspects of cybersecurity, including the motivations and techniques of cybercriminals.
Chapter 4: Incident Response and Recovery
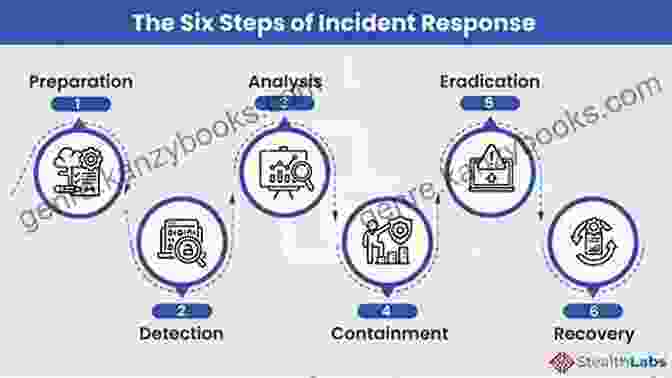
Despite the best cybersecurity measures, incidents can still occur. This chapter provides a comprehensive guide to incident response and recovery, outlining the steps involved in detecting, containing, and mitigating cybersecurity breaches. It also discusses the importance of business continuity planning and disaster recovery strategies for minimizing the impact of cybersecurity incidents.
Chapter 5: The Future of Cybersecurity
Cybersecurity is a constantly evolving field, with new threats and challenges emerging on a regular basis. This chapter explores the latest trends and developments in cybersecurity, including the rise of artificial intelligence, blockchain technology, and quantum computing. It also discusses the future implications of cybersecurity for individuals, organizations, and society as a whole.
'How Cybersecurity Really Works' is an essential resource for anyone seeking to understand the complexities of cybersecurity. Whether you are a cybersecurity professional, a business leader, or simply a curious individual interested in protecting your digital life, this book provides a clear and accessible roadmap to navigating the challenges and opportunities of the cybersecurity landscape. By empowering ourselves with knowledge, we can collectively strengthen our defenses against cyber threats and safeguard our digital world for generations to come.
Additional Resources
- Cybersecurity and Infrastructure Security Agency
- FBI Cyber Division
- Security Industry Association
- ISC2 – International Information Systems Security Certification Consortium
Image Alt Attributes
4.7 out of 5
| Language | : | English |
| File size | : | 7876 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 200 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Neal Graham
Neal Graham Papatia Feauxzar
Papatia Feauxzar Leora Kuttner
Leora Kuttner Leanne Spencer
Leanne Spencer Loretta Sponsler
Loretta Sponsler Tara Caimi
Tara Caimi Thomas Moore
Thomas Moore Lisa Wheeler
Lisa Wheeler Tim Spector
Tim Spector Leonel L Mitchell
Leonel L Mitchell Kathleen S
Kathleen S Mark Singleton
Mark Singleton Lisa Barr
Lisa Barr Yvonne Yazbeck Haddad
Yvonne Yazbeck Haddad Rebecca Hood
Rebecca Hood Leigh Tate
Leigh Tate Ralph Cornish
Ralph Cornish Lindsay Pearson
Lindsay Pearson Lewis Howes
Lewis Howes Richard J Foster
Richard J Foster
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Fyodor DostoevskyHomeopathy Hering Guiding Symptoms: The Essential Guide to Natural Healing
Fyodor DostoevskyHomeopathy Hering Guiding Symptoms: The Essential Guide to Natural Healing
 Jerome BlairUnleashing the Power of Faith Amidst Adversity: "Rock Hard Faith From Rock...
Jerome BlairUnleashing the Power of Faith Amidst Adversity: "Rock Hard Faith From Rock... Natsume SōsekiFollow ·16.5k
Natsume SōsekiFollow ·16.5k Mark TwainFollow ·17.5k
Mark TwainFollow ·17.5k Rod WardFollow ·18.8k
Rod WardFollow ·18.8k Samuel WardFollow ·14.4k
Samuel WardFollow ·14.4k Marvin HayesFollow ·4.7k
Marvin HayesFollow ·4.7k Tom HayesFollow ·10.1k
Tom HayesFollow ·10.1k Emanuel BellFollow ·2.4k
Emanuel BellFollow ·2.4k Gerald BellFollow ·11.1k
Gerald BellFollow ·11.1k

 Houston Powell
Houston PowellThe Chishtis Sufi Masters Of India: Unraveling the...
Immerse Yourself in the...

 Boris Pasternak
Boris Pasternak173 Recipes for the Food You Want to Eat Right Now: A...
Indulge in a Culinary Odyssey: Explore a World...

 Cruz Simmons
Cruz SimmonsUnlock the Power of Shared Leadership: Explore "The...
Empowering Women to...

 Isaac Bell
Isaac Bell120 Essential Recipes to Feed the Whole Crew: Fueling...
In a world where time is precious and mealtime...
4.7 out of 5
| Language | : | English |
| File size | : | 7876 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 200 pages |